Technology
Threats faced in Information technology
Cybercrime is the biggest concern, the world is facing right now. They will continue to evolve and change as time progresses. With the advent of technology in every aspect, the cybercrime has also increased two folds.
We have talked about Information Technology and its benefits to us but we often overlook the gloomy and dark side to it.
Let us explore the bad side of the pitch, the adverse effects of technology. Cybercrime is also on the rise due to the technical faults of our software developers.
The threat from the new technology
Nowadays every other day there is a launch of a new technology be it a new kind of laptop, Smartphone or tablet. In the haste of developing and launching the new products in the competitive technological world, the developers often overlook security issues. The weakly designed technologies are now turning to become a big threat to the world giving rise to more cybercrime. The wrong-doers easily take advantage of the loopholes in the new technology and misuse it.
The threat from inadequate security
Before adopting any cyber security system, you should always check its features so that it’s good enough to deal with all cyber threats. If it does not suffice the requirement, it’s futile.
The threat of using a personal device
There are many instances when you are sharing confidential data with another device. Always use encryption technique in-built in most operating systems to prevent hacking and misuse of confidential data.
The social media attacks
This technique is known as water holing. Today we all have a good social presence in the form of Facebook, Twitter, Instagram etc. There is so much information clustered all over the internet that it is a big threat to our profiles being hacked.
To get some more deep knowledge about Android apps, one should enroll themselves for Android App Development training in Gurgaon, Delhi for the development of students career growth. It will provide you with complete practical knowledge about how actually you should be carefully handling these platforms while using it.
Mobile Malwares
With the increased connectivity of our mobile phones to the internet, there is more threat of mobile malware. If your mobile does not have good malware protection you stand at high risk.
Third party threat
Proper configuration of your security system is very essential to save your business network from threats. Recently New York Times faced a huge threat and as a result lost thousands of clients.
Social engineering threat
You should never befriend a stranger on internet nor share your personal information. Hackers use social engineering skills quite often to hack information.
Outdated security system
Frequently updating your system is very essential. If you do not do so, an outdated security system is futile and it just means giving an open invitation to cyber threats.
A supreme experienced knowledge with certified Web Development course in Gurgaon, Delhi will be very helpful to get trained from the experts and practical hands on learning the technical aspects will be beneficial to you. Not only the development of a web but the various ways we can prevent the cyber threat through technology for the good is been taught for the students knowledge to grow them with practical inherent.
This post should not discourage you from using technology. It should create more awareness and alertness in you. You should realise that you need to keep alert and use your devices and internet safely.
News
Elon Musk Announces Tesla Robotaxi To Be Unveiled On August 8

In a surprising turn of events, Elon Musk announced that Tesla will introduce its much-awaited Robotaxi on August 8, 2024. Interestingly, Musk has a never-ending desire to introduce more self-driving vehicles; however, his dream has not been fulfilled.
Now, the billionaire has announced his plans for Robotaxi on his self-owned platform. He simply wrote on X, “Tesla Robotaxi unveil on 8/8,” and did not give further details about the product.
Moreover, Musk has always been quite vocal about his plan for a car that requires no human control. Not long ago, he shared a tweet about cars with full self-driving features.
He wrote,
Most people still have no idea how crushingly good Tesla FSD will get.
It will be superhuman to such a degree that it will seem strange in the future that humans drove cars, even while exhausted and drunk!
Cars will take you where you want automatically, just like getting in an…
— Elon Musk (@elonmusk) March 29, 2024
In April 2019, Musk first discussed his vision for Robotaxis and revealed that Tesla expects to start its operation in 2020. Clearly, it did not happen.
However, Musk had also shared his unpredictable timetable. He said,
Only criticism, and it’s a fair one, [is that] sometimes I’m not on time.
But I get it done, and the Tesla team gets it done,
Several reports suggest that the Robotaxi news was shared with the employees in February of this year, and they were ordered to shift their entire focus to Robotaxis. urstoryiq.com This also led to a decrease in the production volume of entry-level vehicles.
After Elon Musk’s tweet on April 6, 2024, his company’s shares increased by more than 3%. Notably, Tesla’s shares dropped significantly in the last quarter because of the constantly increasing competition.
See also : Beyoncé Earns Eighth No. 1 Album On Billboard 200 With ‘Cowboy Carter’
Education
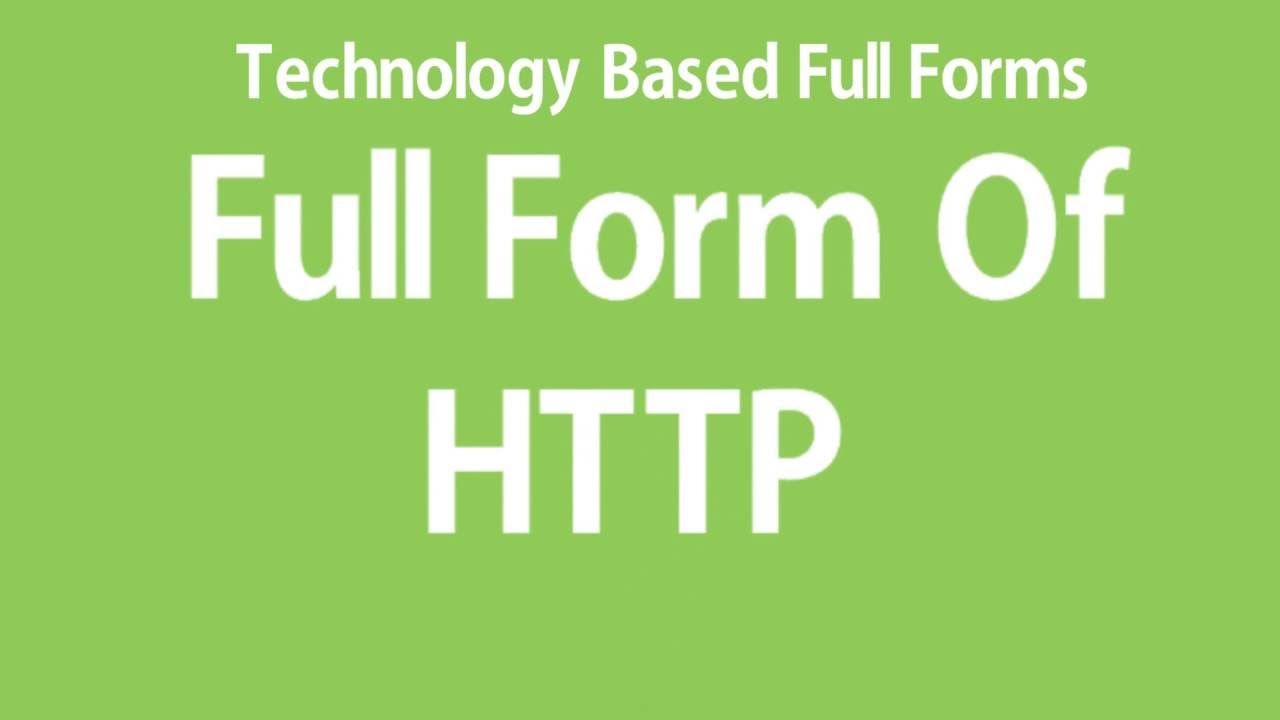
Full Form of http || HTTP Full Form

The HTTP Full Form: The Protocol for Internet Communication 4 you
The HTTP Full Form is Hypertext Transfer Protocol. HTTP is one of the fundamental building blocks of the World Wide Web. Its complete form is Hypertext Transfer Protocol, and it was created in 1989 by Tim Berners-Lee. HTTP is a communication protocol that lets you browse web pages, images, videos, and other media stored on servers in different parts of the world without downloading them to your device.
Definition and Overview of HTTP || full form of http
Education
HCL Full Form: Unveiling the IT Giant’s Identity
-
Technology6 years ago
Developing Workplace Face Recognition Devices and Controls
-

 Business News5 years ago
Business News5 years agoFacts to know about commercial closing
-
Home Advice6 years ago
Things to Remember When Shopping For Recycled Plastic Adirondack Chairs
-
Technology6 years ago
Use WhatsApp Web Login on PC
-
Entertainment6 years ago
Meanings of WhatsApp Symbols, Emoticons
-

 Education5 years ago
Education5 years agoHuman Body And Its Interesting Features
-
Entertainment6 years ago
Ganesh Chaturthi Songs (Mp3, DJ Songs, Remix) Ganpati Songs Free Download
-

 Sports News4 years ago
Sports News4 years agoHow to Build a Perfect Fantasy Cricket Team?









