Technology
Digitalisation & Private Cloud dominate big-time Enterprises
The digital transformation is speeding-up the business activities, operational models and processes to completely embrace the growing opportunities and technological changes. This concept isn’t wholly unusual as there’ve been debates about it for many years. Paperless offices, IT consumerisation, user experience, BYOD and more are finest examples often considered as stepping stones towards the digital world.
User/customer behaviour and innovative technology is driving business digitalisation and so do the demand of private cloud. The transformation also depends on how enterprises cope with the change and can improve overtime without compromising productivity and quality services. As we speak, key players in the IT world including business managers and organisations taking relevant decisions must ask following questions.
- How the tech innovation will bring value to the firm?
- Is transformation easy or rather arduous and may follow restructure from scratch?
- Digitalisation; is it in compliance to the laws, security aspects and demands of the business clients?
- How long will it be effective and the need for retransform?
The revolution isn’t just the domain of big-time companies anymore as smaller organisations, being more nimble realises the true potential of digital tech and process efficiency they muster. Entities regardless of their size look upon at this strategy as a path to improvement and serve the customers in a better way.
The other-way-around approach
Digitalisation allow processes to be reconfigured fundamentally for instance, combination of automated decision making alongside the self-service can eliminate manual procedures. Successful digitalisation efforts start by outlining the future condition for each process without considering the present constraints; it shortens processing time from days to mere minutes.
As soon as the alluring future state has been described, legal restrictions on both digital technologies including private cloud can be reinstated. Companies should accept the challenges these limitations bring and work their way within the defined boundaries. Most are just corporate myths that can be resolved rather quickly through simple discussions.
Manage customer experiences
Going digital with particular levels of customer services may also increase efficiency in selected areas while addressing trendy customer issues. However, it won’t deliver an entirely seamless experience and the result is neglecting significant potential. To manage end-to-end procedure like digitalising support teams for every function in the customer experience, on-board customer and more. But it’s a two-way game where active involvement of the end customer also matters and not just challenging the orthodox wisdom. The cross-functional unit on the contrary follows the direction to defy the present situation. The true spirit of team effort can be achieved with improved communication from clients and consumers.
Foster capabilities
For something that has gone viral over the last few years, digitalisation skills are scarce with successful programs only emphasising over in-house capabilities. The goal is exploiting the best available digital talent at its best to speed-up the internal operations rather than waiting for external resource. Still, there’re times when companies do search for better talent that fits with the new roles and sets like user-experience designers or data scientists.
Agility
Traditional IT-oriented programs usually deliver plausible results only at the end of a particular project which sometimes take years even after the project has been kicked start. Digitalising the end to end process one after another may improve performance in only three to five months. Sophisticated challenges like that of legacy-systems integration can be less agile but there’re ways to mitigate the delay. Exploit low-cost offshore resources to retransfer data among systems introduces a new digital customer procedure online along with a strong IT interface in parallel.
Shifting isn’t always easy and it’s mostly business decision making that causes the bottleneck instead of IT development. This is the reason digitalisation should be based on strong corporate support to deal with stakeholders whereas other decisions must be delegated to the respective project team.
Conclusion
Digital transformation is challenging and businesses must be able to ask the right questions on which based a certain decision with respect to technologies. Private cloud computing and other such services are a few examples with which companies must be familiar with.
News
Elon Musk Announces Tesla Robotaxi To Be Unveiled On August 8

In a surprising turn of events, Elon Musk announced that Tesla will introduce its much-awaited Robotaxi on August 8, 2024. Interestingly, Musk has a never-ending desire to introduce more self-driving vehicles; however, his dream has not been fulfilled.
Now, the billionaire has announced his plans for Robotaxi on his self-owned platform. He simply wrote on X, “Tesla Robotaxi unveil on 8/8,” and did not give further details about the product.
Moreover, Musk has always been quite vocal about his plan for a car that requires no human control. Not long ago, he shared a tweet about cars with full self-driving features.
He wrote,
Most people still have no idea how crushingly good Tesla FSD will get.
It will be superhuman to such a degree that it will seem strange in the future that humans drove cars, even while exhausted and drunk!
Cars will take you where you want automatically, just like getting in an…
— Elon Musk (@elonmusk) March 29, 2024
In April 2019, Musk first discussed his vision for Robotaxis and revealed that Tesla expects to start its operation in 2020. Clearly, it did not happen.
However, Musk had also shared his unpredictable timetable. He said,
Only criticism, and it’s a fair one, [is that] sometimes I’m not on time.
But I get it done, and the Tesla team gets it done,
Several reports suggest that the Robotaxi news was shared with the employees in February of this year, and they were ordered to shift their entire focus to Robotaxis. urstoryiq.com This also led to a decrease in the production volume of entry-level vehicles.
After Elon Musk’s tweet on April 6, 2024, his company’s shares increased by more than 3%. Notably, Tesla’s shares dropped significantly in the last quarter because of the constantly increasing competition.
See also : Beyoncé Earns Eighth No. 1 Album On Billboard 200 With ‘Cowboy Carter’
Education
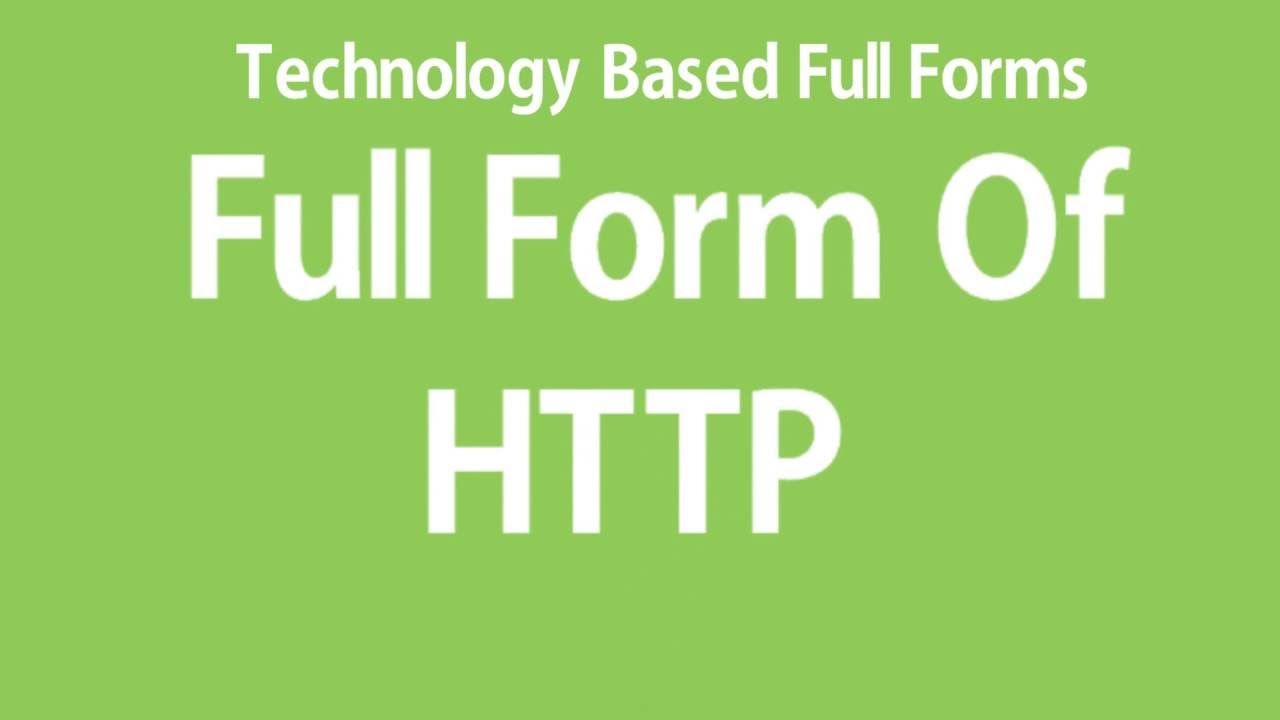
Full Form of http || HTTP Full Form

The HTTP Full Form: The Protocol for Internet Communication 4 you
The HTTP Full Form is Hypertext Transfer Protocol. HTTP is one of the fundamental building blocks of the World Wide Web. Its complete form is Hypertext Transfer Protocol, and it was created in 1989 by Tim Berners-Lee. HTTP is a communication protocol that lets you browse web pages, images, videos, and other media stored on servers in different parts of the world without downloading them to your device.
Definition and Overview of HTTP || full form of http
Education
HCL Full Form: Unveiling the IT Giant’s Identity
-
Technology6 years ago
Developing Workplace Face Recognition Devices and Controls
-

 Business News5 years ago
Business News5 years agoFacts to know about commercial closing
-
Home Advice6 years ago
Things to Remember When Shopping For Recycled Plastic Adirondack Chairs
-
Technology6 years ago
Use WhatsApp Web Login on PC
-
Entertainment6 years ago
Meanings of WhatsApp Symbols, Emoticons
-

 Education5 years ago
Education5 years agoHuman Body And Its Interesting Features
-
Entertainment6 years ago
Ganesh Chaturthi Songs (Mp3, DJ Songs, Remix) Ganpati Songs Free Download
-

 Sports News4 years ago
Sports News4 years agoHow to Build a Perfect Fantasy Cricket Team?









